3.2. Requirements for Kerberos v5 Authentication
The OpenAFS distribution ships with its own implementation of Kerberos v4 and although it is Kerberos v5 capable, it relies on third-party Kerberos v5 libraries. The OpenAFS 1.4 series (and later) integrates with Heimdal or MIT Kerberos for Windows 2.6.5 and above. OpenAFS Kerberos v5 capable functionality includes integrated logon, the AFS Authentication Tool, the Network Identity Manager AFS provider, and the aklog command. These tools provide support for Kerberos v5 authentication including acquisition and automatic renewal of AFS tokens as well as support for single sign-on via the Microsoft Windows Kerberos Logon Service.
The recommended versions of Heimdal and MIT Kerberos for Windows are distributed by Secure Endpoints Inc.. As of this writing, the Secure Endpoints Inc. distribution provides 64-bit Windows support which is unavailable from MIT. KFW 3.2.2 includes Network Identity Manager 1.3.1 which integrates with the AFS Provider installed as part of OpenAFS for Windows. The most recent version of Network Identity Manager is version 2.1 which is available as an independent upgrade to MIT Kerberos for Windows. Heimdal does not include a version of Network Identity Manager.
With Heimdal or Kerberos for Windows installed, the OpenAFS for Windows client can perform authentication to AFS services using Kerberos v5 service tickets as AFS tokens. When a Kerberos v5 derived AFS token is used, all of the AFS Volume Location and File Servers within the authenticated cell must support Kerberos v5. If a Kerberos v5 based token is presented to an AFS server that does not support them, the server will be unable to respond to the client. Attempts to access AFS volumes stored on such a server will fail with the Windows STATUS_NO_KERB_KEY (0xC0000322L) error. Kerberos v5 based tokens are supported by OpenAFS revisions 1.2.8 or later. IBM AFS 3.6 servers do not support Kerberos v5.
3.2.1. Active Directory
Microsoft Windows Active Directory can be used as a Kerberos v5 KDC in conjunction with OpenAFS.
-
There are two things to consider when using an Active Directory as the Kerberos realm that issues the AFS service ticket. First, the Kerberos v5 tickets issued by Active Directory can be quite large when compared to tickets issued by traditional UNIX KDCs due to the inclusion of Windows specific authorization data (the Microsoft PAC). If the issued tickets are larger than 344 bytes, OpenAFS 1.2.x servers will be unable to process them and will issue a RXKADBADTICKET error. OpenAFS 1.4 (and beyond) servers can support the largest tickets that Active Directory can issue.
-
Second, the Kerberos v5 tickets issued by Windows 2003 Active Directory are encrypted with the DES-CBC-MD5 encryption type (enctype). OpenAFS 1.2.x servers only support the DES-CBC-CRC enctype. As a result, OpenAFS 1.2.x servers cannot process the resulting Kerberos v5 tokens. Windows 2000 Active Directory issues tickets with the DES-CBC-CRC enctype. Windows Server 2008 R2 Active Directory domain by default disables use of DES-CBC-MD5 and it must be enabled.
Microsoft has documented in Knowledge Base article 832572 a new NO_AUTH_REQUIRED flag that can be set on the account mapped to the AFS service principal. When this flag is set, the PAC authorization data will not be included in the ticket. Setting this flag is recommended for all accounts that are associated with non-Windows services and that do not understand the authorization data stored in the PAC. This flag cannot be used if AFS service tickets are obtained via cross-realm using an Active Directory user principal.
Note that an Active Directory computer object cannot be used for the afs service principal. A user object must be used.
-
Starting with Windows 7 and Windows Server 2008 R2, Microsoft has disabled the single DES encryption types,TechNet: Changes in Kerberos Authentication. DES must be enabled via Group Policy in order for Active Directory to be used as a KDC for OpenAFS. Enable weak encryption becuase of AFS... Start > Administrative Tools > Group Policy Management Expand Forest > Domains > (domain name) > Group Policy Objects > Default Domain Policy Right-click "Default Domain Policy" and select "Edit" Expand "Computer Configuration" > "Policies" > "Windows Settings” > "Security Settings” > "Local Policies” > "Security Options” Double click "Network security: Configure encryption types allowed for Kerberos” Select "Define this policy setting", then select "DES_CBC_CRC" and all the others... Press "OK"
3.2.2. The krb524 Service is no longer supported
Before there was native support for Kerberos v5 derived AFS tokens, the krb524 service was used to convert a Kerberos v5 service ticket into a Kerberos v4 service ticket that could in turn be used to construct an AFS authentication token. As of OpenAFS 1.2.8 [14 December 2002], support was added to allow the immediate use of Kerberos v5 tickets as AFS (2b) tokens. This is the first building block necessary to break away from the limitations of Kerberos v4 with AFS. By using Kerberos v5 directly the security holes inherent in Kerberos v4 cross-realm are avoided. Use of cryptographically stronger algorithms for authentication and encryption become a possibility.
Another reason for using Kerberos v5 directly is because the krb524 service runs on port (4444/udp), which has increasingly been blocked by Internet service providers. The port was used to spread a worm which attacked Microsoft Windows in the Summer of 2003. When the port is blocked users find that they are unable to authenticate.
Replacing the Kerberos v4 ticket with a Kerberos v5 ticket is a win in all situations except when the cell name does not match the realm name and the principal names placed into the ACL's are not the principal names from the Kerberos v5 ticket. Unfortunately, some organizations have AFS cell names and Kerberos realm names which differ by more then just typographic case and rely the krb524d service to map the Kerberos v5 client principal name from realm FOO to a Kerberos v4 principal in realm BAR. This allows user@FOO to appear to be user@bar for the purposes of accessing the AFS cell.
To support this mode of operation OpenAFS for Windows versions 1.4.x through 1.6.x supported a registry value, Use524, that forced the use of krb524d within the AFS Authentication Tool and during integrated logon. Previous revisions of this documentation advised that this option should only be used by individuals until such time as their organizations transitioned away from the krb524 service.
Over the last few years all Kerberos distributions have removed support for Kerberos v4. As a result, OpenAFS can no longer support the krb524d service and the functionality has been removed from the source tree for the 1.7.x release.
As an alternative, sites should be aware that the OpenAFS 1.4.x servers permit the use of a secondary realm name that can be treated as equivalent to the cell name for authentication. This functionality can be used to avoid the need for the krb524 service if and only if both realms are managed by the same administrative entity.
3.2.3. Network Identity Manager Provider
As of release 1.5.9, OpenAFS for Windows includes a Network Identity Manager Provider for obtaining AFS tokens. This plug-in is a contribution from Secure Endpoints Inc. Network Identity Manager is a multiple identity credential management tool that ships with MIT Kerberos for Windows version 3.0 and above. The OpenAFS plug-in requires Heimdal or MIT Kerberos for Windows version 3.1 or above.
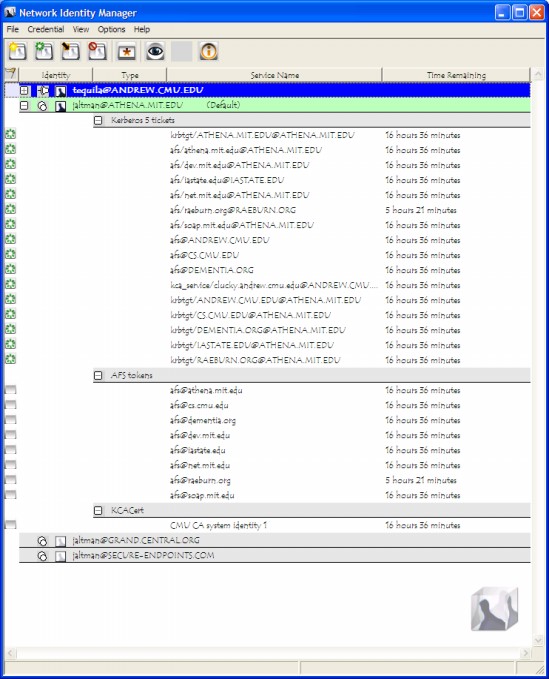
The Network Identity Manager replaces the former KFW 2.6.x ticket manager, "Leash", and when combined with the OpenAFS Provider it can be used as a replacement for the AFS Authentication Tool (afscreds.exe). Unlike both Leash and the AFS Authentication Tool, Network Identity Manager with the OpenAFS Provider can easily acquire and renew AFS tokens for multiple cells from one or more Kerberos v5 identities.
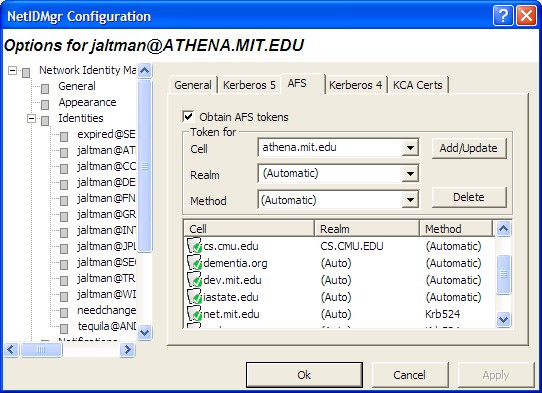
The AFS configuration panel for each Kerberos v5 identity is used to configure which cells credentials should be obtained for and how they should be obtained. If the cell to realm mapping cannot be automatically determined, it can be explicitly specified. If the cell does not support Kerberos v5 tickets as tokens, then a krb524 service can be configured.
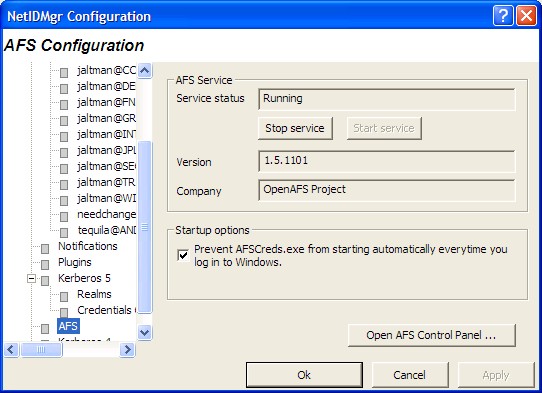
The OpenAFS Provider configuration panel can be used to check the status of the AFS Client Service and its version. An optional checkbox is provided that will prevent the AFS Authentication Tool from being started by Windows after login. A shortcut to the OpenAFS Control Panel is also provided.
As of OpenAFS 1.5.66, the Network Identity Manager OpenAFS Provider displays the same AFS Lock notification icon generated by the AFS Authentication Tool. The AFS Lock can be used to determine if:
-
one or more AFS tokens are valid
-
no AFS tokens are present but the AFS service is running
-
the AFS Service is not running
-
the AFS Service is running but there is a communication error preventing access to \\AFS
3.2.4. Heimdal 1.5, MIT 4.x, and Weak Encryption Types
Just as Microsoft disabled the use of Weak Encryption Types in Windows 7 and Windows Server 2008 R2, Heimdal and MIT have disabled the use of weak encryption types in their latest releases. In order to use Heimdal 1.5 or MIT Kerberos 1.9 or later with OpenAFS, the weak encryption types including DES-CBC-CRC and DES-CBC-MD5 must be enabled. In Heimdal, this is performed by adding "allow_weak_crypto = true" to the [libdefaults] section of the %SystemRoot%\ProgramData\Kerberos\krb5.conf file. In MIT KFW 4.x, this is performed by adding "allow_weak_crypto = true" to the [libdefaults] section of the %SystemRoot%\ProgramData\MIT\Kerberos5\krb5.ini file.
Futures versions of OpenAFS will not have this requirement.